How to Keep Your Online Business Safe in 2022
The COVID-19 pandemic has made modern businesses depend on technology more than ever. As the adoption of technology by businesses continues to rise, these businesses generate and process large volumes of...
IOTransfer 3 Review – iPhone Transfer Software
Many people want to make a backup of their iPhone data on the computer and keep them safe. iTunes or iCloud can perform functions like data transfer and backup of the...
Why Do Websites Need the Security Services?
If you run an online business it is vitally important that your site has the best security possible for many reasons:
First Impressions
Your website is your brand, your storefront, and often your...
Best Laptops for College Students in 2020
Previously, students wrote all the work manually, and, in principle, they did not need laptops. However, whatever one may say, now a student can use a laptop for a lot of...
Here’s How You Can Spot a Fake Crypto Investment Scam
As a new form of investment, cryptocurrency has drawn considerable attention. But here's the thing: fraudsters prey on people's understanding or lack thereof of cryptocurrency investments and how they operate. Younger...
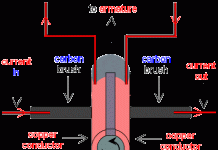
What is a Slip Ring Commutator? Composition, Types, Alternative Uses & Names
A slip ring commutator is an electromechanical tool. It allows the transmission of electrical signals and power from a device that is stationary to another device that is rotating. It is...
Best Practices to Implement Continuous Testing
Since the inception of mobile apps, the entire world has experienced huge digital transformation. The influence of mobile apps has transformed our lifestyles. It has made our lives much faster, convenient,...
A Comprehensive Guide to Network Vulnerability Assessment
Imagine that you're getting a network infrastructure that already has all of its custom software and hardware resources configured to set up. Waiting for your network's weaknesses to get exploited before...
Why Every Business Must Care About Visual Content for Social Media
The word visual content might sound like a buzzword. After all, content is content. It doesn’t matter what medium you deliver it through, so why does the distinction between visual content...
(Top 5) Steps to Creating an Online Presence for Your Brand
The importance of having an online presence in today's competitive market cannot be overemphasised. This is because an online presence can make or break your business, especially for small to mid-sized...